DNS over HTTPS |
Created | ||
|---|---|---|---|
| Updated | |||
| Author | Nicolas Dorriere | Reading | 3 min |

I publicly provide 2 DNS server endpoints using the HTTPS protocol. This means that the communication between your terminal and my DNS servers will be encrypted. If someone attempts a Man-in-the-Middle attack using mitmproxy, bettercap, or a simple tcpdump on port 53, they will be unable to see your traffic.
My servers use Adguard and Technitium as DNS software continuously updated.
The Adguard endpoint is useful for dispersing your DNS requests across more than 60 DNS over HTTPS servers, all hosted in Europe with extremely low latency. I have benchmarked each of them to create a curated list that respects privacy.
The Technitium endpoint is a unique DNS over HTTPS server, which can be useful for filling your list of dispersed servers, such as the one I offer above.
Regarding privacy, I host both services in separate LXC containers on my own equipment, connected to a low-latency fiber connection. I anonymize all IP addresses that connect to my DNS servers. I do not exploit any data and do not look at logs - I have better things to do... life is short
🔮 Random Upstream
Software: AdGuard Home - v0.107.63
Endpoint: https://doh-random-upstream.nicolas-dorriere.fr/dns-query
Features AdGuard Home:
- DNS over HTTPS (reverse caddy TLS)
- self-hosted in France
- adblock
- no filter
- no logging
- IP anonymized
- load-balancing mode
- dilution max 5%
- cache
- dashboard not exposed to internet
- dns request ~90ms
Features Public Upstream: (65 servers 🇪🇺)
- DNS over HTTPS
- keeps DNS traffic inside Europe
- 200ms max
- pure recursion (no upstream)
- no Cloudflare
- no Google
Blocklists
AdGuard DNS filter
https://adguardteam.github.io/HostlistsRegistry/assets/filter_1.txt
Steven Black's List
https://adguardteam.github.io/HostlistsRegistry/assets/filter_33.txt
Malicious URL Blocklist (URLHaus)
https://adguardteam.github.io/HostlistsRegistry/assets/filter_11.txt
Phishing Army
https://adguardteam.github.io/HostlistsRegistry/assets/filter_18.txt
uBlock filters – Badware risks
https://adguardteam.github.io/HostlistsRegistry/assets/filter_50.txt
Dilution
What is dilution? I've adopted this term to simply explain that each DNS request is systematically sent to a different DNS server, thus avoiding any notion of centralization by a single entity and reinforcing privacy.
The DNS servers of Cloudflare (1.1.1.1) or Google (8.8.8.8) concentrate too many DNS requests. They use your data to likely serve ads for Google, and for Cloudflare, likely to improve their products. 1.1.1.1 remains the recursive DNS server with the lowest latency in the world, ahead of Google and others.
The percentages in the table below show the number of requests dispatched to the different DNS servers present in Adguard's list. For example, for the server collecting the most requests, NextDNS, they will see a maximum of 4% of my DNS traffic. The public DNS server of DNSFORGE sees only 2.68% of my traffic.
We avoid centralization, as mentioned earlier, and achieve dilution.
The more servers we have in our dilution list, the better your privacy will be.
DNS over HTTPS servers with low latency and respect for privacy (no logging, anonymization) are rare. That's why I offer a public endpoint to help improve the global privacy of internet users.
Dilution list (last update 24/11/25)
58 servers 🇪🇺
https://doh.kel.pe/
https://dns.aa.net.uk/dns-query
https://dns.a47.me/dns-query
https://dns.brahma.world/dns-query
https://dns.braene.com/dns-query
https://dns.csaonline.de/dns-query
https://dns.busold.ws/dns-query
https://dns.caspervk.net/dns-query
https://dns.csa-rz.de/dns-query
https://dns.datenquark.de/dns-query
https://dns.digitalsize.net/dns-query
https://dns.dnshome.de/dns-query
https://dns.dremaxx.de/dns-query
https://dns.faked.org/dns-query
https://dns.fancyorg.at/dns-query
https://dns.floriantinney.de/dns-query
https://dns.froth.zone/dns-query
https://dns.gamban.com/dns-query
https://dns.glf.wtf/dns-query
https://dns.hostux.net/dns-query
https://doh.immerda.ch/dns-query
https://dns1.in-berlin.de/dns-query
https://dns.switch.ch/dns-query
https://dns.artikel10.org/dns-query
https://doh1.b-cdn.net/dns-query
https://ns.data.haus/dns-query
https://dns.digitale-gesellschaft.ch/dns-query
https://3dns.eu/dns-query
https://masters-of-cloud.de/dns-query
https://dukun.de/dns-query
https://dns.luma-medien.com/dns-query
https://doh.ffmuc.net/dns-query
https://dns.kernel-error.de/dns-query
https://dns.kescher.at/dns-query
https://eu1.dns.lavate.ch/dns-query
https://public.ns.nwps.fi/dns-query
https://doh.niyawe.de/dns-query
https://adguard-kartoffel.zernico.de/dns-query
https://doh.lv/dns-query
https://dns.nick-slowinski.de/dns-query
https://dns.njal.la/dns-query
https://dns.novg.net/dns-query
https://dnspub.restena.lu/dns-query
https://dns.silen.org/dns-query
https://dns.smartguard.io/dns-query
https://dns.vaioswolke.xyz/dns-query
https://doh.zknt.org/dns-query
https://odvr.nic.cz/dns-query
https://adfree.usableprivacy.net/dns-query
https://dns.skrep.eu/dns-query
https://yarp.lefolgoc.net/dns-query
https://eu.tri-dns.net/dns-query
https://dns.roedel.cloud/dns-query
https://resolver.sunet.se/dns-query
https://dns.t53.de/dns-query
https://dns.tls-data.de/dns-query
https://abel.waringer-atg.de/dns-query
https://ns2.4netguides.org/dns-query
< WIP put stats dilution >
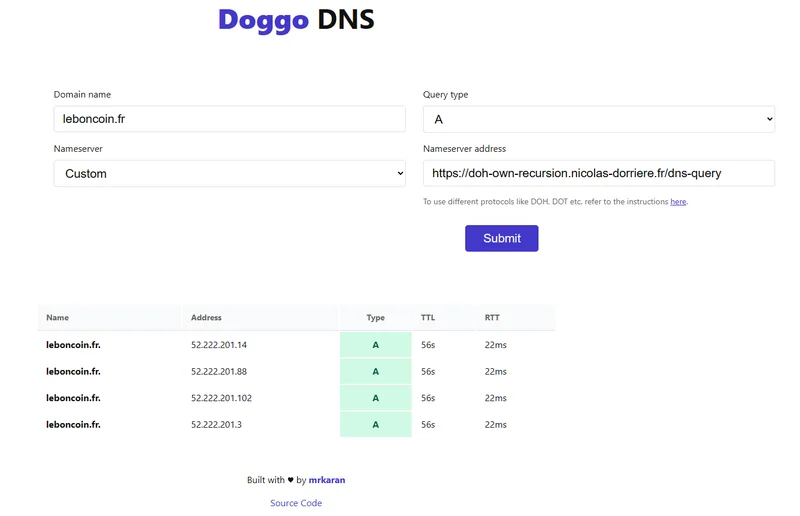
🍭 Own Recursion
Software: Technitium v13.6
Endpoint: https://doh-own-recursion.nicolas-dorriere.fr/dns-query
Features Technitium:
- DNS over HTTPS (reverse caddy TLS)
- DNSSEC
- Self-hosted in France
- Pure recursion (no upstream) (ICANN root server)
- No logging
- No filter
- Dashboard not exposed to internet
- Cache (10k website 30/06/25)
- Speed (benchmark locate : From Deutschland VPS Hetzner Falkenstein)
- nocache ~200ms
- cache ~130ms
Features Public Upstream: no public upstream
Misc.
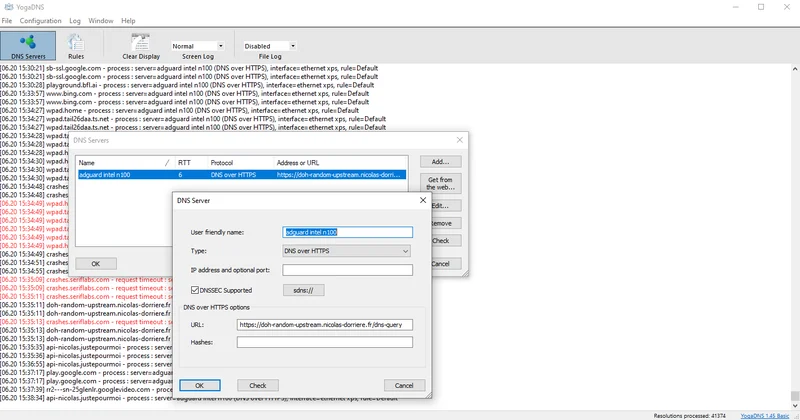
https://github.com/frankovo/dns-benchmark-tool
ClientsI'm using YogaDNS on Windows to connect to my DoH servers; the free version is more than enough.
What is DNSSEC? Dive into DNSimple's fun, illustrated comic to learn all about it!