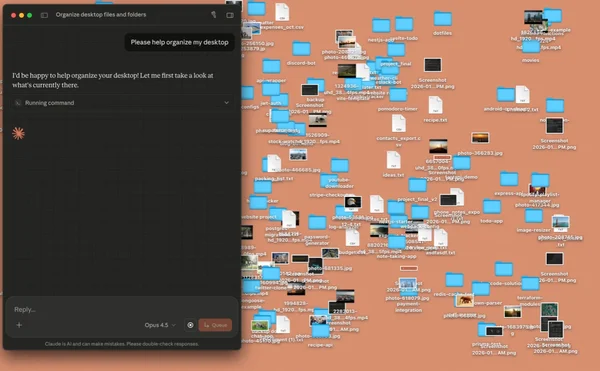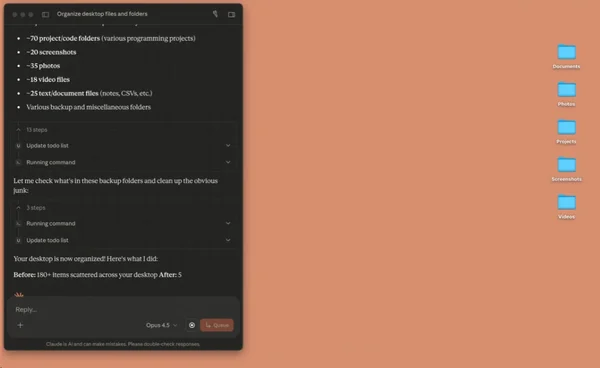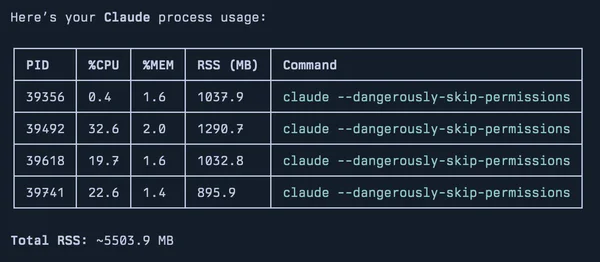
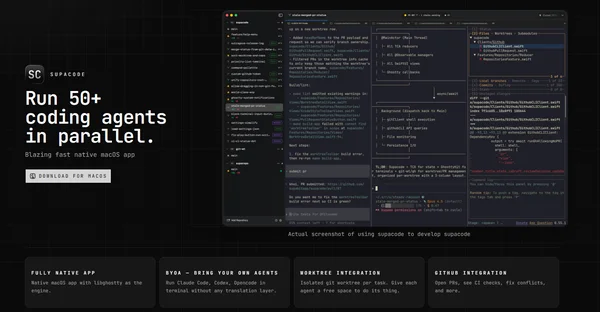
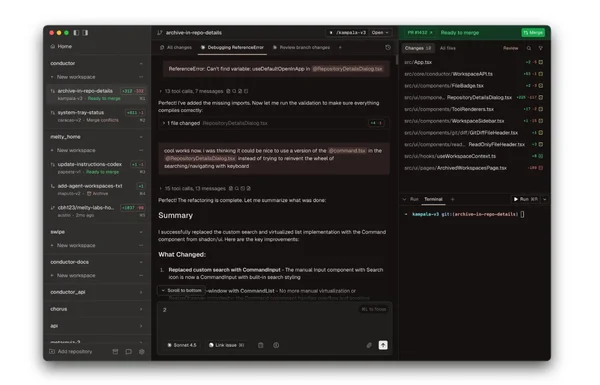
Supacode
Isolation workspace : git worktree
Isolation runtime : no
Native macOS app with libghostty as the engine
Run Claude Code, Codex, Opencode in terminal without any translation layer
Isolated git worktree per task. Give each agent a free space to do its thing
Open PRs, see CI checks, fix conflicts, and more
Isolation runtime : no
Conductor clones it and works entirely on your Mac
Each Claude Code you spin up gets an isolated workspace
See who's working, what needs attention, and review code
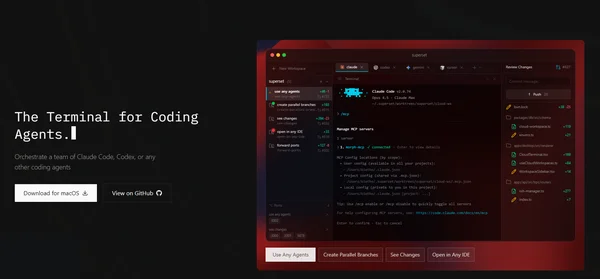
Superset
Isolation workspace : git worktree
Isolation runtime : no
Launch multiple AI coding agents across different tasks. Work on features, fix bugs, and refactor code — all in parallel.
Superset is agent-agnostic. Use Claude Code, OpenCode, Cursor, or any CLI-based coding tool. Switch between agents seamlessly.
Each agent runs in its own isolated Git worktree. No merge conflicts, no stepping on each other's changes. Review and merge work when you're ready.
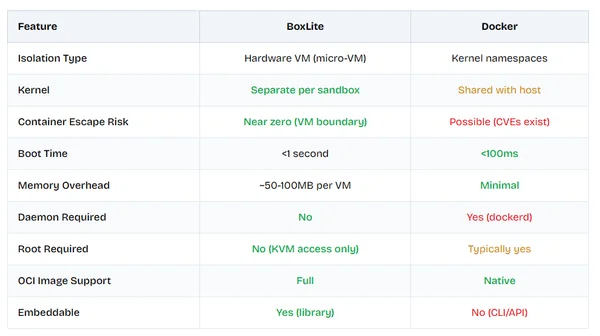
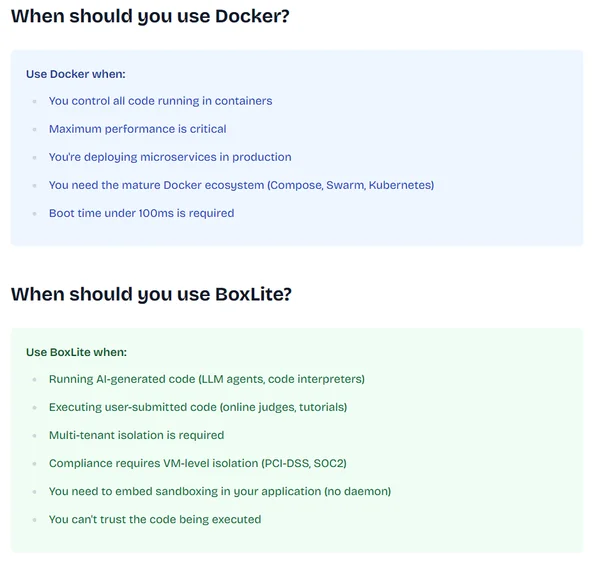
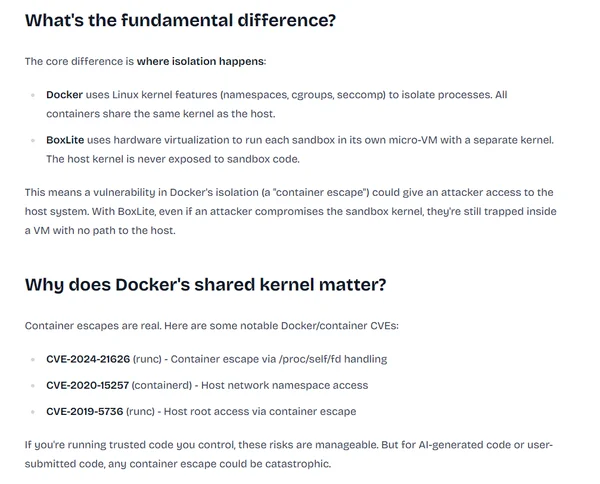
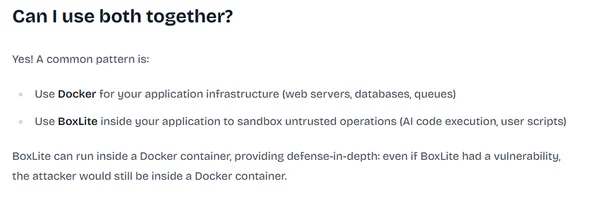
BoxLite
Isolation workspace : no
Isolation runtime : MicroVM
BoxLite lets you spin up lightweight VMs ("Boxes") and run OCI containers inside them. It's designed for use cases like AI agent sandboxes and multi-tenant code execution, where Docker alone isn't enough and full VM infrastructure is too heavy.

Rivet
Isolation workspace : git worktree
Isolation execution : no
State survives crashes, restarts, and process termination
Broadcast events to all connected clients as they happen
Retrieve full session history for debugging or analysis
Run thousands of concurrent agent sessions across your infrastructure

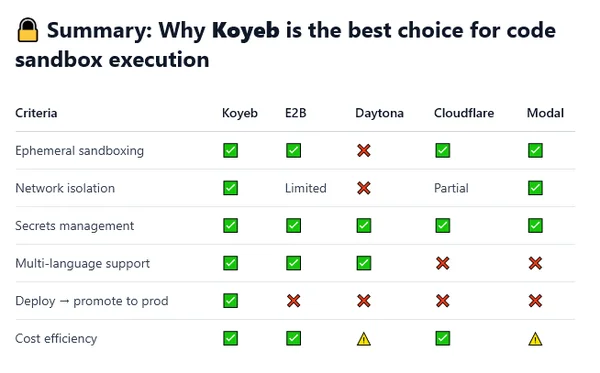
Koyeb
Isolation workspace : no
Isolation runtime : MicroVM
Fast, Scalable, Fully Isolated Environments for AI Agents and More
At Koyeb, we provide high-performance serverless infrastructure for intensive applications across CPUs, GPUs, and accelerators. We take code, build it, and run it in fully isolated, secure microVMs on bare-metal servers around the world. We scale automatically when needed, down to zero when idle, with cold starts as low as 250ms.
koyeb.com/blog/koyeb-sandboxes-fast-scalable-fully-isolated-environments-for-ai-agents
Sandboxes are ideal for:
Ϟ Running AI agents and workflows in fully isolated environments
Ϟ Executing untrusted or user-generated code securely
Ϟ Prototyping applications quickly
Ϟ Testing APIs or libraries in clean environments
Ϟ Demonstrating functionality without configuring local infrastructure

CPU
2x Intel® Xeon® Silver 4309Y
(8C/16T ea., up to 2.8GHz, 105W)
Memory
512GB (16x32GB)
DDR4-3200 ECC RDIMM
(12 Slots Free)
Storage
3.8TB U.2 NVMe PCIe 4.0 x4
Tensor Processors
4x Tenstorrent Wormhole™ n300s Tensor Processor (Jim Keller)
4x Warp 100 Interconnects
Power Supply
1+1 Titanium Level PSUs
1200W: 100-127Vac
1800W-2090W: 200-240Vac
2200W: 220-240Vac (200V input or higher input voltage required)
Base System
SuperMicro SuperServer SYS-740GP-TNRT


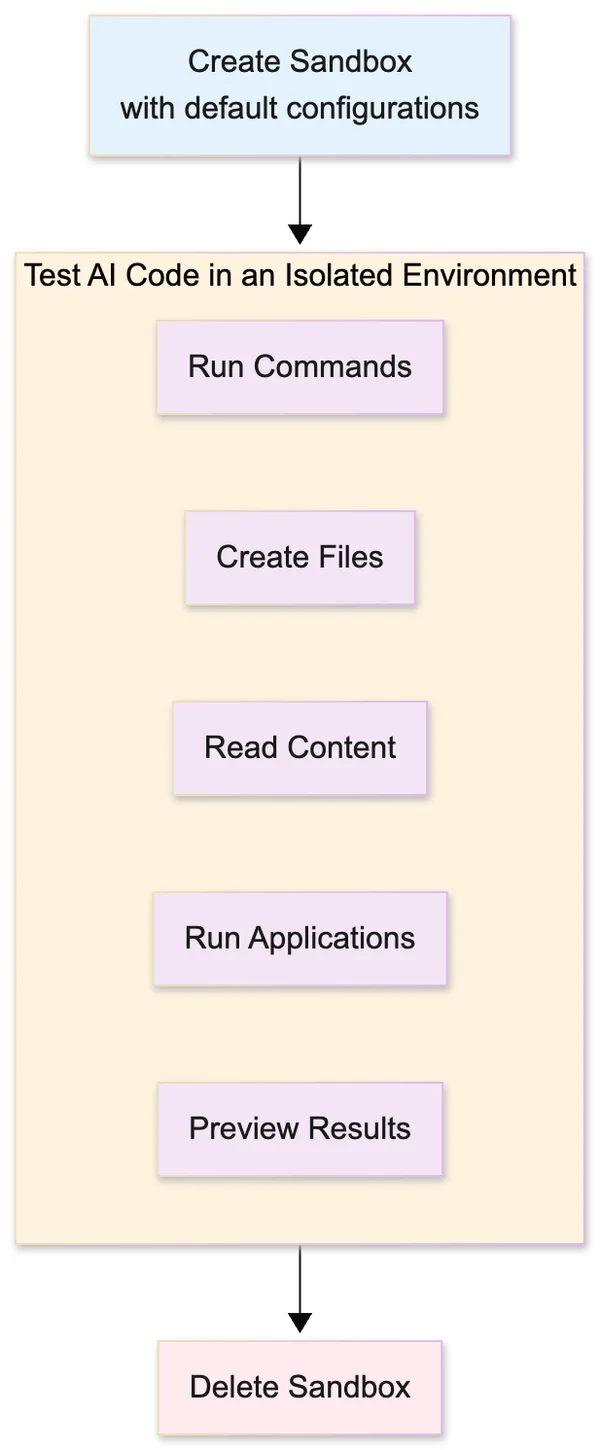
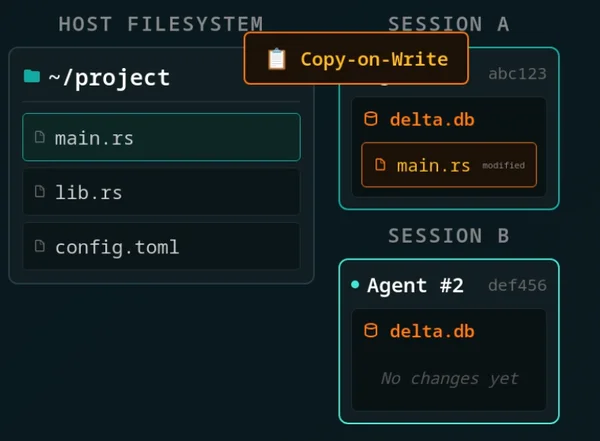
AgentFS
AgentFS provides isolated filesystem access backed by a SQLite file so agents can safely run the CLI tools they were trained on.
TUI agentic coding
Opencode ᖊ
curl -fsSL https://opencode.ai/install | bash
᛭ opus, gpt, gemini, grok, (kimi, qwen, deepseek, glm, devstral)
Claude code ᖊ
curl -fsSL https://claude.ai/install.sh | bash
᛭ opus
Amp ᖊ
curl -fsSL https://ampcode.com/install.sh | bash
᛭ opus, gpt, gemini, grok, (kimi, qwen, deepseek, glm, devstral)
Mistral Vibe
curl -fsSL https://mistral.ai/vibe/install.sh | bash
᛭ devstral
Crush
npm install -g @charmland/crush
᛭ opus, gpt, gemini, grok, (kimi, qwen, deepseek, glm, devstral)
Codex
npm install -g @openai/codex
᛭ opus, gpt, gemini, grok, (kimi, qwen, deepseek, glm, devstral)
Copilot
npm install -g @github/copilot
᛭ gpt, opus, grok
* ᖊ = cool

Building a TUI to index and search my coding agent sessions
stanislas.blog/2026/01/tui-index-search-coding-agent-sessions/

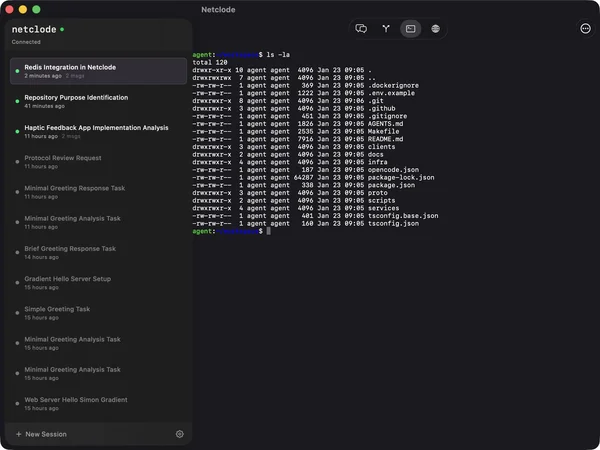
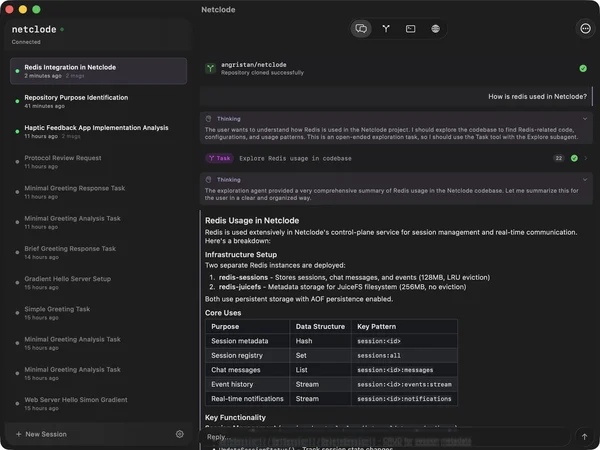
Netclode
Isolation workspace : git worktree
Isolation runtime : MicroVM (kata)
If you are exploring autonomous coding agents like Claude Code or OpenCode, you need to check out Netclode by @angristan. It’s a self-hosted platform designed to run these agents securely on your own infrastructure and accessible via iOS
Running an AI agent that executes arbitrary code on your machine can be risky.
Netclode solves this by wrapping sessions in Kata microVMs:
Provisioning: Swift commands k3s to create a Pod.
Runtime: k3s uses Kata Containers instead of runc.
Virtualization: Cloud Hypervisor starts the micro-VM.
Execution: The agent runs in complete security.
Destruction: Once finished, the VM is deleted, leaving no trace.
It is the perfect architecture for safely unleashing the power of AI coding assistants.
https://github.com/angristan/netclode
https://stanislas.blog/2026/02/netclode-self-hosted-cloud-coding-agent
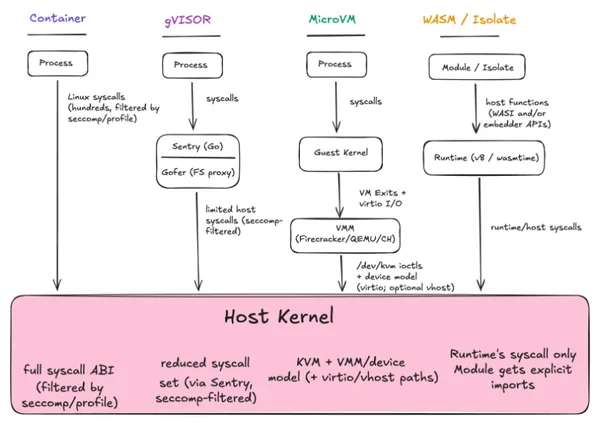
A field guide to sandboxes for AI
arts 🦇
Playground Engine, a Firecracker-powered microVM orchestrator

Boot Linux microVMs in <1s - for sandboxes and services.
Firecracker
slicervm.com
Kata Containers
exe.dev

Popularization of the infinitesimally small with the help of Blender software. State of the art!
2022-2024 : chat
2024-2025 : agentic coding
2026-2027 : agentic admin (9-5 desk job)