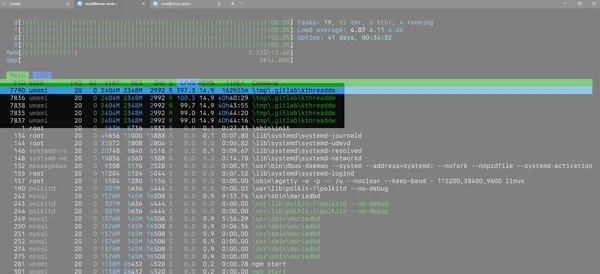
I got hit by ‘React2Shell (CVE-2025-55182)’, and my little Intel N150 ended up mining Monero for 4 days. Luckily, my Umami app was running in an unprivileged LXC container under Incus
I deleted the container, then recreated a new one with the Next.js patch in Umami version 3.0.3. I carefully checked all the processes on my Incus Arch Linux host, and there was no container escape :-]
I’m thinking of vibecoding a small alerting system to detect abnormal CPU usage.
The same thing happened to this person on a Hetzner server.
https://blog.jakesaunders.dev/my-server-started-mining-monero-this-morning
https://news.ycombinator.com/item?id=46305585
However, I feel sorry for users running non-rootless Docker with solutions like Coolify or Dokploy
Docker can automatically modify iptables and open host ports. Example: docker run -p 8080:80 nginx exposes port 8080 on the host, potentially bypassing firewall rules and making the service reachable from the internet. Docker is powerful, but not secure by default. Always review exposed ports and bind to localhost when possible.